Welp, attacker’s are finding new ways to evade threat detection and weaponize social engineering, according to a new Netskope Cloud and Threat report that analyzes malware intelligence every quarter. The new snack of choice? You guessed it, cloud applications.
The threat landscape is evolving as the number of malware families and variants are constantly expanding. In Q1 alone, Netskope detected more than 60,000 distinct malware samples — A steep 72% of which were new malware families or new variants of existing families, confirming that threat detection is quite the challenging problem for enterprises.
Invisibility cloak
Attackers are becoming more comfortable abusing cloud services by infiltrating network services widely used in an enterprise, according to Netskope. Crowded channels act as a sort-of semi-invisible invisibility cloak, where threat actors can blend in with normal traffic and avoid enterprise firewalls.
Cloud apps especially are becoming an attractive space for attackers to deploy malware. Cloud malware downloads have seen quarter-over-quarter increases since Q1 2022, which Netskope expects to continue through 2023.
An uptick in cloud malware downloads is to blame for this spike, specifically from the most popular enterprise cloud apps — cloud storage apps such as Amazon S3 and Google Drive, but also collaboration apps, free software hosting services, web hosting services and webmail apps, such as Gmail.
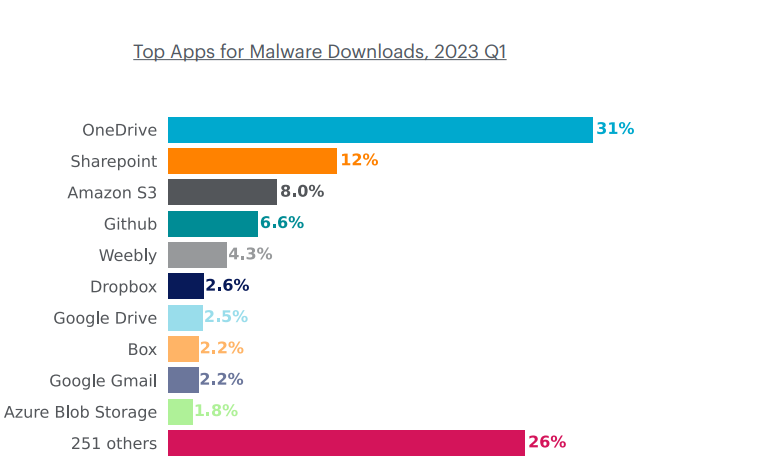
When it comes to the creme de la creme of malware paradise, however, that title is held by Microsoft OneDrive, which continues its multi-year stand at the top of the malware download list, “a position it is poised to retain throughout 2023,” according to Netskope.
Attackers are also feeding into cloud app abuses as a form of social engineering — attackers will use app features familiar to victims to trick them into downloading malware. Netskope attributes social engineering to at least 73% of malware infiltration attempts.
Inspect. Your. Stack.
So, how does one steer clear of cloud-munching malware? The most important step is making sure your security stack fully inspects all cloud downloads, “especially downloads from the most popular cloud apps,” wrote Ray Canzanese, director of Netskope Threat Labs to Silverlinings.
“Many of the apps used by attackers to deliver malware are also business-critical; inspection of the downloads from those apps is vital. As an additional step, organizations can reduce their risk surface by blocking apps that are not used in the organization, but that step should be taken in addition to (not instead of) ensuring all downloads are inspected.”
Netskope also pushes “cross-functional collaboration” to combat these malware attacks. On average, five out every 1,000 enterprise users attempted to download malware in Q1 2023, according to Netskope — cross-functional collaboration must boil responsibility all the way down to an individual contributor of a company.

